Why Cybersecurity Is Mission-Critical in 2025
Cyber threats are no longer a distant possibility—they’re a daily reality for businesses of all sizes. As ransomware-as-a-service (RaaS) grows more sophisticated, and AI-driven attacks become harder to detect, companies across Tulsa and beyond face increasing risk.
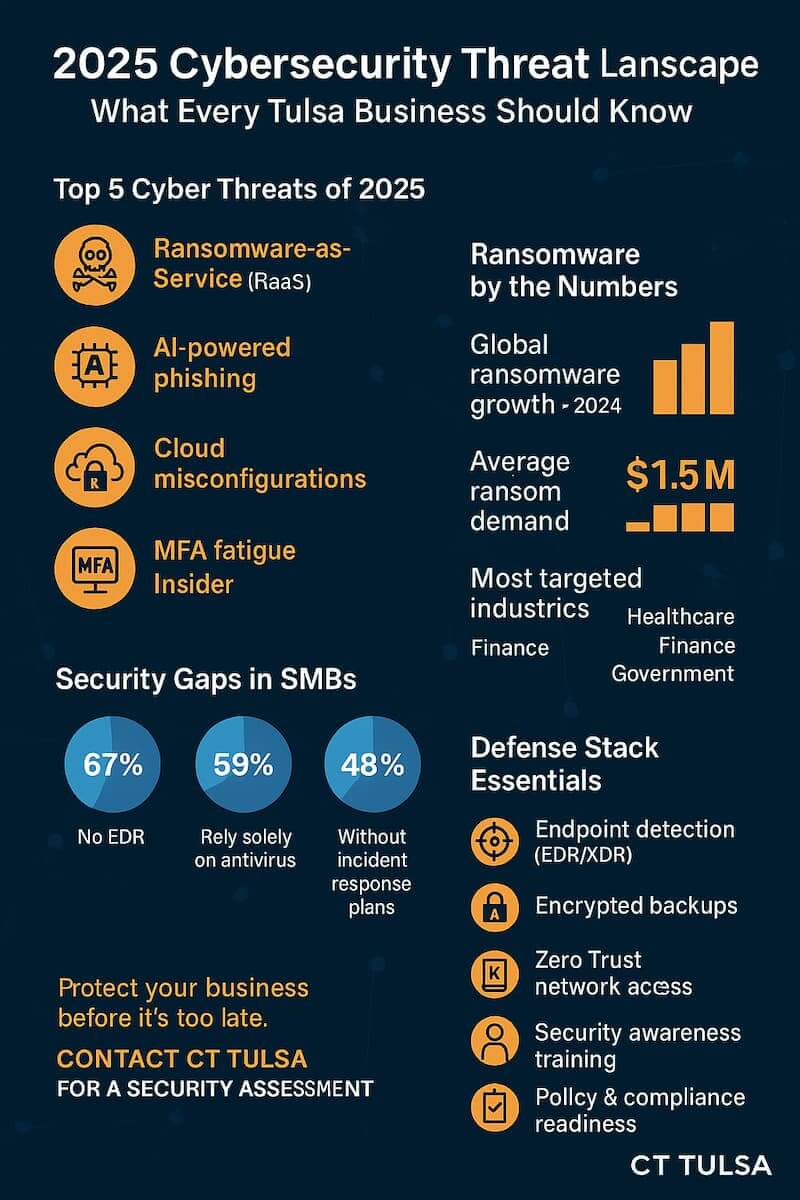
In 2024 alone, ransomware attacks surged by 95% globally, with SMBs among the top targets (IBM Security). As we move into 2025, the stakes are higher than ever. This article breaks down the most critical cybersecurity and ransomware trends shaping the landscape and offers expert strategies for protecting your organization, especially if you operate in or around Tulsa.
Trend #1: Ransomware-as-a-Service (RaaS) Is Industrializing Cybercrime
Once the domain of elite hackers, ransomware attacks are now widely available as pay-to-use kits. Known as Ransomware-as-a-Service, these toolkits are making it easy for non-technical criminals to launch sophisticated attacks.
Key stats:
- RaaS attacks now account for 60–70% of all ransomware incidents (ENISA Threat Landscape 2024).
- Average ransom demands exceeded $1.5 million in Q4 2024.
- Double extortion, encrypting and stealing data, has become the default approach.
Impact on Tulsa businesses: Local SMBs, healthcare clinics, and municipalities have increasingly become soft targets due to outdated defenses and limited IT staff. Without proactive cybersecurity solutions, a single ransomware attack could cripple operations.
Trend #2: AI Is Powering Both Sides of the Cyber War
Artificial Intelligence is revolutionizing cybersecurity, but it’s also arming attackers. AI-generated phishing emails, automated vulnerability scanning, and deepfake scams are rising fast.
“AI tools are enabling attackers to scale and personalize attacks at speed. Defensive AI must evolve just as fast.” — Maya Horowitz, Check Point Software Technologies
Recommendation: Implement AI-powered threat detection like Endpoint Detection & Response (EDR), which continuously learns from threat behavior. Combined Technology’s Cybersecurity Services include advanced EDR solutions tailored for SMBs.
Uncertain about which IT service model fits your business best?
Our team is here to help you navigate the options and answer all your questions so you can make the best decision for your business. Get in touch for a free assessment today!
Trend #3: Cloud and Remote Work Environments Remain Vulnerable
With cloud adoption and hybrid work now standard, cybercriminals are targeting platforms like Microsoft 365, Google Workspace, and VPNs.
- Misconfigured cloud settings cause over 45% of data breaches.
- MFA fatigue (repeated login prompts) is being exploited to trick users into giving access.
Best practices for Tulsa teams:
- Enforce Zero Trust access policies
- Use multi-layered authentication (not just basic MFA)
- Routinely audit cloud permissions
If you need guidance implementing cloud security best practices, Combined Technology’s managed IT services can help strengthen your infrastructure.
Trend #4: Geopolitical Cyber Threats Are Escalating
Nation-state and state-sponsored hacking groups are increasing attacks on critical infrastructure, energy sectors, and supply chains—many of which involve Oklahoma-based logistics and manufacturing companies.
- The FBI has warned about increased ransomware targeting American municipalities.
- Sectors like education, utilities, and public health are high-priority targets.
Local action point: Combined Technology helps secure business-critical systems with network segmentation, incident response planning, and compliance support tailored for high-risk sectors.

Trend #5: Compliance and Cyber Insurance Are Raising the Bar
Regulatory requirements are growing stricter, and cyber insurance providers are demanding more from businesses.
New developments:
- SEC rules now require public companies to disclose material cyber incidents within 4 days.
- FTC Safeguards Rule updates impact any business handling customer data.
- Insurers are refusing coverage unless firms implement MFA, backups, and risk assessments.
Combined Technology Tulsa offers:
- Cyber risk assessments
- Compliance support for HIPAA, FTC, GDPR, and NIS2
- Business continuity and disaster recovery planning
How Tulsa Businesses Can Defend Themselves in 2025
Here’s a checklist of cybersecurity essentials every SMB in Tulsa should implement:
Cyber Defense Checklist
- Advanced threat detection (EDR/XDR)
- Zero Trust access policies
- Encrypted and frequent cloud backups
- Cybersecurity awareness training
- Patch management automation
- Incident response plan
- Cyber insurance readiness assessment
Pro Tip: Don’t wait until you’re under attack. Schedule a cybersecurity consultation with Combined Technology to assess your current defenses.
Expert Insight: “Cybersecurity is a Business Risk – Not Just an IT Problem”
Cybersecurity no longer lives in the server room, it’s a boardroom topic. From reputational damage to legal liability, the consequences of inaction are massive.
“The fastest-growing risk in 2025 is executive inaction. Businesses that don’t treat cybersecurity as a strategic priority will find themselves paying a premium—whether through ransom payments or lost trust.”
— Alex Stamos, Former CSO, Facebook
Future-Proof Your Business Against Ransomware
Cyber threats in 2025 aren’t slowing down—and ransomware is only getting smarter. But with the right defenses, tools, and team in place, you don’t have to live in fear of the next breach. Partner with a cybersecurity provider that understands the unique needs of Tulsa businesses. Contact Combined Technology today to start building a resilient, future-proof cybersecurity posture.
Frequently Asked Questions
What is ransomware-as-a-service (RaaS)?
RaaS is a business model where cybercriminals lease ransomware tools to affiliates, who then carry out attacks and share profits. It’s made ransomware far more accessible and widespread.
How can I tell if my business is a ransomware target?
If your business stores sensitive data, relies on uptime, or has legacy systems, you are a target. Small and mid-sized businesses are often hit because of weaker defenses.
How often should we update our cybersecurity protocols?
At least quarterly, and after any major system change or cyber incident. Regular risk assessments are essential.
What makes Combined Technology different from other cybersecurity providers?
Combined Technology offers locally focused, deeply personalized service for Oklahoma businesses—combining national-level expertise with hands-on support and tailored compliance solutions.
Get in Touch with Us

Safeguard Your Business with Tulsa's Top Managed IT Provider
At Combined Technology, we provide a flexible, tailored approach to meet your evolving IT needs. Safeguard your business against emerging threats with our expert-managed IT services and customized cybersecurity solutions.





