Organizations of all sizes are moving critical systems and data to the cloud, but many are still treating cloud security as an afterthought. There’s a persistent misconception that cloud providers handle all security needs or that cloud environments are inherently more secure than traditional setups. The reality? Both cloud and on-premise infrastructures carry serious risks. And both require equally strong security strategies.
What’s Changing: From Servers to Services
The way companies operate has shifted dramatically. Instead of relying solely on physical servers in office data centers, businesses now use a mix of cloud services, hybrid infrastructure, and remote access tools. This evolution creates new entry points for cyber threats, and demands new ways of thinking about security.
Cloud vs. On-Prem Security: How They Differ
Here’s how the two environments compare:
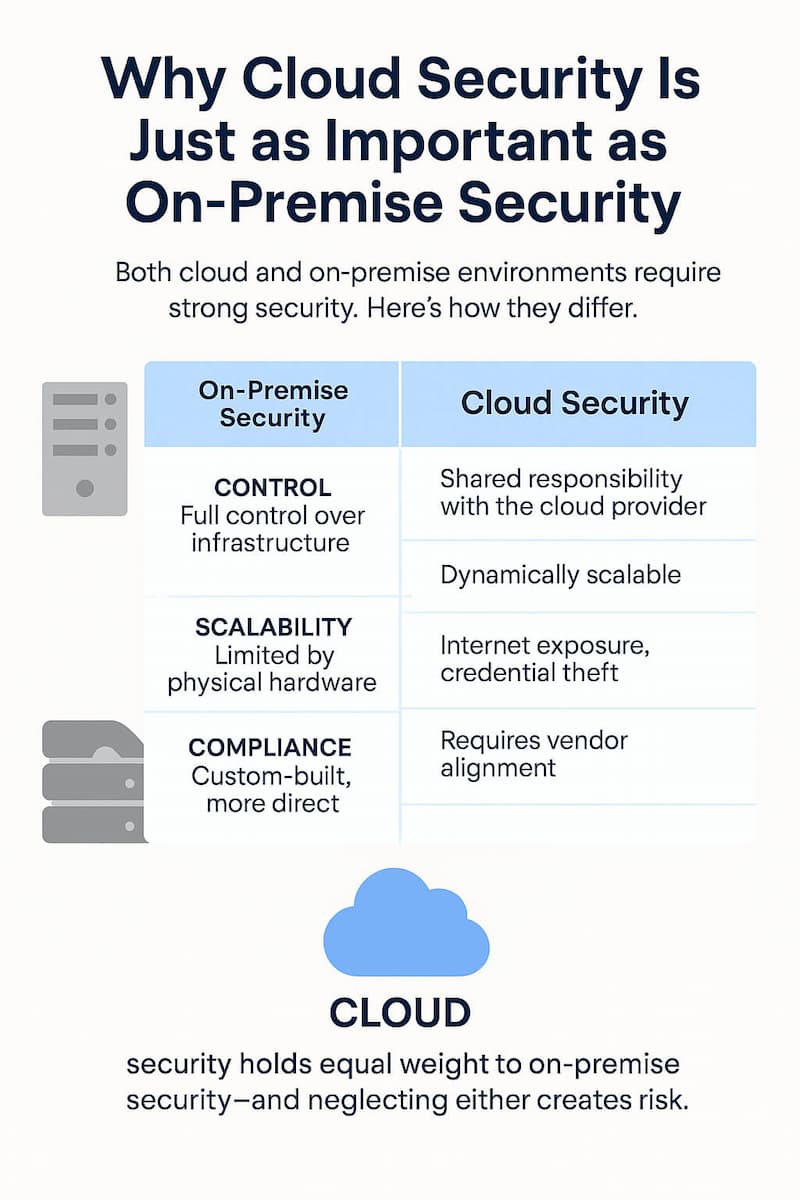
| Factor | On-Premise Security | Cloud Security |
| Control | Full control over infrastructure | Shared responsibility with the cloud provider |
| Scalability | Limited by physical hardware | Dynamically scalable |
| Threat Vectors | Local network threats, physical breaches | Internet exposure, credential theft |
| Compliance | Custom-built, more direct | Requires vendor alignment |
Uncertain about which IT service model fits your business best?
Our team is here to help you navigate the options and answer all your questions so you can make the best decision for your business. Get in touch for a free assessment today!
Why Cloud Security Is Essential
You’re Still Responsible for Your Data
Cloud providers secure the infrastructure, but you’re responsible for user access, data, and app-level controls. This is part of the Shared Responsibility Model, a concept many businesses overlook.
Breaches Are Increasing in the Cloud
Cloud misconfigurations and poor access management are now among the top causes of breaches. Gartner estimates that 99% of cloud security failures will be due to user error through 2025.
Regulations Don’t Differentiate
Whether your data lives on a local server or in the cloud, compliance rules like HIPAA, GDPR, and CCPA still apply. Failing to secure either can lead to steep fines and reputational damage.
How to Secure Cloud Environments
To match or exceed your on-premise security standards, adopt these cloud-specific practices:
- Use Zero Trust principles: Always verify user identity, device status, and access level.
- Encrypt everything: Data at rest and in transit should be encrypted by default.
- Enable MFA: Strong authentication dramatically reduces the risk of credential theft.
- Monitor continuously: Use native tools like AWS CloudTrail or Microsoft Defender to detect unusual activity.
- Train employees: Most breaches start with human error. Educated users are your first line of defense.
Why On-Premise Security Still Matters
While cloud platforms are gaining traction, many companies still run mission-critical applications on physical infrastructure. These systems face their own challenges, such as outdated software, physical access risks, and manual updates.
Key on-prem security must-haves include:
- Regular patching and vulnerability management
- Strong firewall and network segmentation
- Physical security controls in server rooms
- Disaster recovery and backup procedures
Real-World Scenario: A Hybrid Gap
One healthcare company suffered a data leak after misconfiguration cloud storage buckets, even though its on-prem systems were tightly locked down. The oversight led to exposed patient data, fines, and a costly compliance investigation. The takeaway: a weak cloud setup can compromise your entire IT posture.
Final Thoughts
Cloud adoption isn’t slowing down, and neither are cyber threats. If your business relies on both cloud and on-prem systems, your security posture should reflect that. Treating cloud security with the same urgency and depth as on-prem is no longer optional. It’s a requirement for staying protected, compliant, and competitive.
Ready to modernize your security stack?
Schedule a consultation with Combined Technology to create a unified, secure infrastructure that covers both cloud and on-prem.
FAQ
What’s the biggest cloud security risk?
Misconfigured access and inadequate visibility. These issues open doors to unauthorized users and accidental data exposure.
Is cloud more secure than on-prem?
Not by default. It depends on how each environment is configured, monitored, and managed.
Can one strategy cover both environments?
Yes, with unified tools like SIEMs and IAM platforms, you can monitor and protect both environments under a single security framework.
Get in Touch with Us

Safeguard Your Business with Tulsa's Top Managed IT Provider
At Combined Technology, we provide a flexible, tailored approach to meet your evolving IT needs. Safeguard your business against emerging threats with our expert-managed IT services and customized cybersecurity solutions.





